With its recent introduction in iOS 16, Lockdown Mode’s effectiveness against sophisticated threats like the Pegasus spyware had yet to be publicly tested. A recent report from Citizen Lab provides the first known case of Lockdown Mode’s efficacy, particularly against an exploit known as PWNYOURHOME.
What is PWNYOURHOME?
PWNYOURHOME is a two-phase zero-click exploit targeting iOS 15 and iOS 16. The first phase exploits the HomeKit functionality (homed process), while the second phase targets iMessage (MessagesBlastDoorService process). The exploit does not require the user to have previously configured a “Home” in HomeKit.
Infiltration: The exploit targets iPhone’s HomeKit and iMessage systems, adding an attacker’s email to HomeKit and deleting an iMessage attachment.
HomeKit Exploitation: It triggers a crash in the homed process by misusing the NSKeyedUnArchiver to decode an unusual class, setting the stage for the exploit.
iMessage Exploitation: Malicious PNG images downloaded via iMessage cause crashes in the MessagesBlastDoorService process, indicating the bypass of pointer authentication codes (PAC).
Gadget Execution: The exploit uses a series of functions, or gadgets, to manipulate memory and execute arbitrary code, bypassing security measures.
Memory Manipulation: A memory copy gadget is employed to copy memory chunks, aiding further exploitation.
Final Execution: The exploit escapes the BlastDoor sandbox and launches the Pegasus spyware via the mediaserverd process.
This is a TLDR, but for those interested in more technical details on the exploit chain, I highly recommend reading the full comprehensive report by Citizen Lab for an in-depth analysis.
Lockdown Mode Prevention
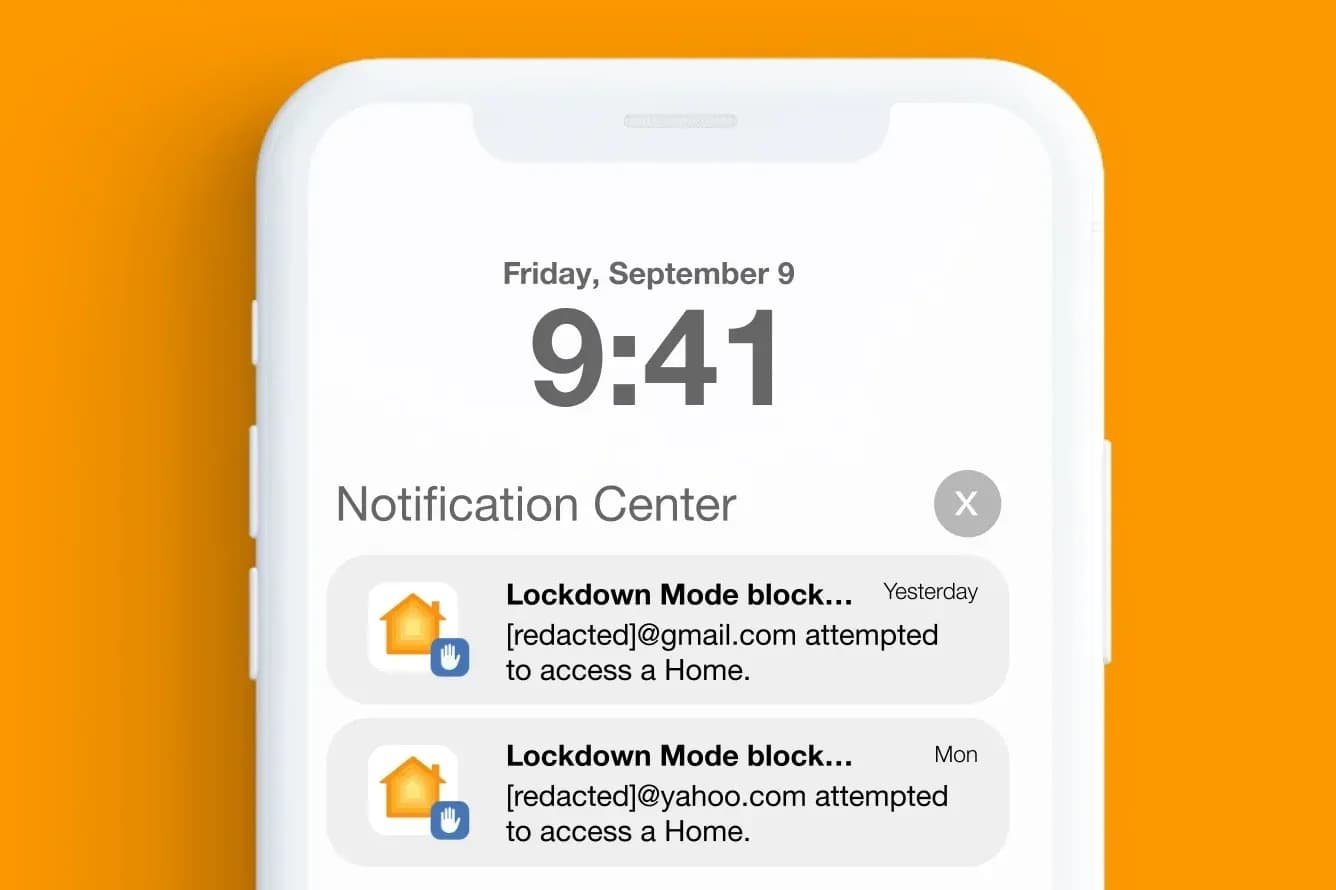 On a device with lockdown mode enabled, the user’s iPhone blocks an attempted HomeKit invitation. Source: Citizen Lab
On a device with lockdown mode enabled, the user’s iPhone blocks an attempted HomeKit invitation. Source: Citizen Lab
When Lockdown mode is enabled, it restricts incoming invitations for Apple services from unknown contacts. Specifically, it blocks unsolicited FaceTime or Home invitations, and promptly notifies the user of such an intervention.
By disallowing invitations from unrecognized sources for services like HomeKit, devices in Lockdown Mode were capable of generating immediate alerts upon detecting exploitation attempts. Although Citizen Lab suspects that PWNYOURHOME may have been modified to circumvent user notifications, there is no evidence of successful infiltrations on devices with Lockdown Mode activated.
While Apple’s task is far from complete, and continuous refinement of Lockdown Mode is necessary, the initial outcomes are encouraging. This represents a victory for potential targets, showcasing that Apple’s implementation is effectively impeding the progression of spyware.
Sources
Ryan Naraine: Curious if these contain bypasses for iOS Lockdown Mode